Teaching and Learning
Unit 1 Applied Computing
Unit 1 Area of Study 1: Data analysis
Outcome 1:
On completion of this unit the student should be able to interpret teacher-provided solution requirements and designs, analyse data and develop data visualisations to present findings
Examples of learning activities
- Prepare a presentation for the class that contains several examples of data, both qualitative and quantitative. In a whole-class discussion, students classify each example as being either qualitative or quantitative. A Kahoot! activity could be used requiring students to classify statements as being either qualitative or quantitative, such as: ‘28% of households shopped at Aldi last month’; ‘Optical sensor detects oxygen saturation level of 96% in a person’s blood stream’; or ‘Many parents feel guilty when buying fast-food’
- Provide students with a recent newspaper article that features a story of interest to them (e.g. from the fields of nutrition, environmental studies, sport, health science or crime) and which contains several distinct pieces of data. Students are required to analyse the news story and extract all data, assigning each piece of data to an appropriate data type. The activity can be undertaken individually or in a small group and results shared with the class.
- Discuss the factors affecting the quality of data and information, such as accuracy, bias, integrity, relevance and reliability. Screenshots of sample data featuring these characteristics are shown to the students who identify the issues with the data samples.
- Watch the short video Analytics in the AFL – The Most Data Rich Sport on Earth. In small groups, students are each assigned a role from the following list: player, coach, football fan, sports journalist. Each group discusses the characteristics of data and information from the perspective of the assigned roles. A spokesperson from each group is nominated to report back to the class, summarising their group’s discussions.
- Students work in small groups to devise three or four questions that can be used to check whether the Australian Privacy Principles are being followed in an organisation. Each group’s list is then combined to create a class list. The questions should relate to the Australian Privacy Principles explicitly mentioned in the study design: Principles 2, 6 and 11.
- Assign students to small groups. Provide each group with a hypothetical scenario such as: ‘A healthcare AI system shares anonymised patient data with a pharmaceutical company to develop new treatments’; or ‘An AI chatbot in a social media app collects user messages to improve its language understanding’. Each group discusses the ethical considerations involved in the scenario, considering guiding questions such as: Is the data collection or sharing justified?; Has user consent been obtained?; What potential benefits and risks are associated with data sharing?; and Are there alternatives to data sharing? Each group shares its thoughts with the class
- Display an article or data source to the class. Students work in teams (pairs or small groups) to create an accurate APA citation for the article or data source. Each team shares their APA citation in Padlet (or similar) with the class. The class discusses each team’s citation, including any errors or omissions.
- Provide students with a case study that contains the need for a data solution. Students engage in a whole-class discussion to discuss and critically analyse the scenario, identifying the functional and non-functional requirements of the proposed solution, the constraints imposed and scope of the proposed solution.
- Provide students with an authentic set of data, possibly from an area of student interest. Examples of authentic data can be found on websites such as: FiveThirtyEight; Bureau of Meterology; and Climate Science. Students identify a guiding question and then create annotated diagrams or mock-ups for a spreadsheet, database and data visualisation. As an extension, students can create data visualisations for the annotated diagrams or mock-ups from the activity.
- Discuss the structural characteristics of relational databases in a teacher-prepared presentation. In a follow-up Kahoot! activity students respond to questions and scenarios on the characteristics of relational databases, where they identify the main features, such as: tables, primary keys, foreign keys and queries.
- Discuss the structural characteristics of spreadsheets in a teacher-prepared presentation. In a follow-up Kahoot! activity students respond to questions and scenarios on the characteristics of spreadsheets, where they identify the main features, such as: rows, columns and cells.
- Students complete a series of database exercises where they: create tables; set up validation rules; enter data; create queries; and test the database. In a follow-up activity, students extract data from a pre-loaded database and import the data into a spreadsheet, before creating a chart or data visualisation
- Provide students with an authentic set of data, possibly from an area of student interest. Examples of authentic data can be found on websites such as: FiveThirtyEight; Bureau of Meterology; and Climate Science. Students upload the authentic data into a spreadsheet and complete a series of exercises where they calculate average, median, count/frequency and standard deviation.
- Students work in groups to locate and analyse an online news story that contains a data visualisation. Each group is to report back to the class, via a multimedia presentation, the results of the analysis, such as: target audience, key information presented in the data visualisation, any inaccuracies or ambiguities and suggested improvements to better inform and persuade the targeted audience.
- Provide students (working individually or in a group) with a different set of data that covers a specific topic or theme (e.g. demographics, sport, economics or the environment). Students are to examine their data sets, identify key trends or patterns that are of interest and create a data visualisation, either as an infographic (long-form), a series of posters of infographics or as a dashboard.
- Adapt the classic game of Pictionary, where students are given data visualisation terms (e.g. pie chart, histogram, bar chart, scatter plot, legend, axis label). Students take turns in drawing these terms on a whiteboard while the rest of the class guesses what they are drawing.
- Prepare a presentation that contains images sourced from a current organisation, such as a government department. Discuss the importance of formats and conventions. Students work collaboratively in small groups, mimicking an organisation, to develop a set of formats and conventions for databases, spreadsheets and data visualisations.
Detailed example
Based on one of the learning activities (KK 14)
Analysis of data visualisations in the media
Data visualisations are important tools to businesses and organisations because they allow the target audience to quickly and easily understand the information being presented. In this activity students are provided with the opportunity to gain an insight into data visualisations in an authentic context, as well as preparing those students planning on undertaking the Units 3 and 4 Data Analytics course. This activity is best suited as a collaborative task, collaboration being a key skill that teachers should foster with their students.
There are two suggested approaches that the teacher can use in running this activity. Firstly, they may provide each student group with the opportunity to search and locate a suitable media article of particular interest to them and which contains a data visualisation. Alternatively, they can provide the online link to the media article containing the data visualisation.
Note: If the teacher opts for student choice in selecting the media article, an initial check of the data visualisation should be undertaken to ensure that it is appropriate for the activity and the student group.
Sample media articles can be found in a variety of fields and sources, such as:
- medicine and health (e.g World Health Organisation)
- climate science (e.g The Australian Institute; Asian Development Bank)
- sport and health science (e.g. Australian Sports Commission)
- business and finance (e.g International Monetary Fund, World Economic Forum).
In this activity, students critically analyse the data visualisation and its context, and report back to the class with their findings. This can take the form of a multimedia presentation. Some factors for each group to consider when compiling their response are:
- the intended audience
- key information being presented and how well it achieves this objective
- any inaccuracies or ambiguities
- suggested improvements to better inform and persuade the targeted audience.
Unit 1 Area of Study 2: Programming
Outcome 2:
On completion of this unit the student should be able to interpret teacher-provided solution requirements to design and develop a software solution using an object-oriented programming language.
Examples of learning activities
- Present students with incomplete code snippets created by an AI code generation tool and then discuss as a class the generated code, evaluate its correctness and compare it to manually written solutions.
- Students develop a list of data types from the Terms used in this study (pages 12–16 of the study design). They research and develop a description for each of the data types in relation to the programming language being studied and give examples for each one.
- Students develop a series of small software solutions that demonstrate the use of data structures, such as one-dimensional arrays, lists and records, and then describe the differences between them.
- Students interpret a short case study in order to prepare a table listing the functional and non-functional requirements of the software solution, as well as the constraints and scope
- Students use design tools, such as mock-ups, IPO charts, flowcharts and pseudocode, to design a software solution in response to a case study. An example of a software solution could involve a payroll system that calculates the gross pay, tax deducted (30% of gross pay), superannuation collected (12% of gross pay before tax) and net pay from the input of hours worked and hourly rate paid.
- Students work in small groups to research and create a multimedia presentation that focuses on issues such as: code plagiarism; code theft; unauthorised distribution of software; software piracy; non-compliance with open-source licenses and the reverse engineering of proprietary software to modify the code.
- To explain abstraction, provide the students with an analogy of a car’s dashboard and how it abstracts complex data from the engine and then have students working in small groups to create their own analogy. In a follow-up activity, use the analogy of a vending machine to explain why encapsulation is needed; users interact with a vending machine through a limited interface (i.e. inserting money/credit card and press a button), while the inner workings (product storage and retrieval) are hidden and protected. Students can then create and share their own analogy to explain encapsulation.
- Students develop a software solution that includes: variables, control structures (sequence, selection, iteration/repetition), arithmetic operators, logical operators, conditional operators, procedures, functions and methods.
- Students list and describe how naming conventions can be used to distinguish solution elements (such as file types, functions, methods and variables) for Hungarian notation and camel casing.
- Provide students with the source code for two different programs. They analyse the code in order to determine what each program does. The first program given to students contains no internal documentation. The second program contains sufficient internal documentation to identify the purpose of the program. Conduct a class discussion examining the purpose of internal documentation and where comments should be placed within a software solution.
- Students complete a series of exercises, such as: a program that simulates user authentication for a system, with the program to check if a given username and password combination exists in a list (existence checking); a program that checks if all elements in a given list have the same data type, and returns ‘true’ if all elements have the same type, otherwise ‘false’ is returned (type checking); a program that validates a user's age when they sign up for a service (range checking).
- Students design a testing table for a software solution that calculates an employee’s pay. Hours worked is entered followed by hourly rate. A value for gross pay is calculated with 12% subtracted for superannuation and 30% for tax. A value for net pay is then calculated. Students determine the expected result in the testing table with a pen and calculator; develop the software solution using a programming language and then test. Test results are noted in the actual result column of the table. These are compared with the expected result to determine if the software solution meets requirements. Students debug if errors are found.
Detailed example
Based on one of the learning activities (KK 3)
Developing software solutions – programming skills development
To assist students who have limited programming knowledge, the teacher could provide them with partially written programs. These programs may consist of missing lines of code, or lines of code that are incomplete, or a combination of both. In the commercial world, not all programs are written from scratch. Instead, many businesses employ an approach involving a type of ‘skeleton’ programming framework, where the program contains common pre-written lines of code but omits the intended functionality of a program. This helps in ensuring consistency in how programs are written in the organisation, which makes the code easier to read and simpler to maintain. For this reason, the teacher could consider providing the less experienced students with skeleton code (i.e. a working program that has had some lines of code removed and/or some lines of code that are only partially written) to help scaffold student learning, especially in the initial stages of the programming area of study.
Examples of practice activities that students might complete are:
- One-dimensional arrays
-
- declare and initialise a one-dimensional array
- insert elements into an array, then print the array.
- loop through an array, printing each element of the array
- change the value of an array element, printing the array before and after the change
- concatenate the elements of the array, then print the result of the concatenation
- declare and initialise a one-dimensional array
- Records and files
-
- open an existing ‘txt’ file, then close it (note: it is a good programming practice to close a file when finished with it)
- open an existing ‘txt’ file, then read a fixed number of characters of the first line (or record) of the ‘txt’ file into a variable which is then printed
- open an existing ‘txt’ file, then read the first line (or record) of the ‘txt’ file into a variable which is then printed
- write a record to a file, creating a new file in the process or replacing an existing file
- append a new record to an existing file
- read the records from an existing file into an array or list, sort the array or list, and then write contents of the array or list to a new/existing file
- use getName (or similar, depending upon the programming language used) to return the name of a file as a string
- delete a file and its contents and rename a file
- develop code for exception handling to test whether a file exists or not.
Note: As part of these programming practice activities, students should use comments to justify their use of appropriate features of the programming language.
Unit 2 Applied Computing
Unit 2 Area of Study 1: Innovative solutions
Outcome 1:
On completion of this unit the student should be able to, in collaboration with other students, identify a problem, need or opportunity to analyse, design, develop and evaluate an innovative solution.
Examples of learning activities
- Assign students to small groups and have each group select one of the UN’s 17 Sustainable Development Goals, one that most resonates with them. Each group brainstorms potential creative and/or innovative ideas and solutions to address their chosen goal. Students develop a project proposal to outline their goal, the specific problem to be addressed and their creative and/or innovative solution. Each group shares their project proposal with the class and the class provides feedback.
- Introduce students to the concept of assistive technologies and how these technologies are designed to help individuals to perform tasks that would otherwise be difficult or impossible. Students then work in small groups to research an assistive technology (e.g. screen readers for the visually impaired, communication devices for non-verbal individuals), and report their findings to the class, which includes the functionality and capability of their assistive technology.
- Students explore the impact, including potential impact, of emerging technologies on society; for example, Tesla’s autopilot, Amazon delivery drones, wearable plant sensors, net-zero-energy data centres.
- Select a range of issues from media resources such as deskilling, job loss and misuse. Divide students into three groups with each group working on one issue. Groups discuss the issue and present what they have learnt to the class.
- Assign students to small groups and provide each group with an image of a past or present-day technology. Examples include: Sony Walkman, SatNav, Sony PlayStation, Nintendo GameCube, iPhone, Apple watch, Nix Hydration Biosensor, Space Invaders game. Each group undertakes a critical analysis through research to identify the characteristics of their product that were innovative when released to the market.
- Prepare a selection of advertisements featuring current or emerging technologies for use in a class discussion. Show each advertisement featuring a different technology to the class who critically analyse them as part of a whole-class discussion. Students discuss what the functional and non-functional requirements, scope and constraints for the technologies would be.
- Discuss, using examples, the techniques for collecting data to determine user needs and requirements, such as interviews and surveys.
- Provide a range of examples to students demonstrating how design tools and techniques such as mock-ups, pseudocode, sitemaps and storyboards can be used for representing designs.
- Conduct a class discussion and demonstrate the development of an innovative solution. Discuss techniques such as getting to know the end user (empathise), brainstorming, mind mapping and ideation.
- Present examples of techniques for documenting the development of solutions, including the tools and techniques for coordinating and monitoring projects, such as Gantt charts. Use OneNote as a project journal for recording the development of the solution (e.g. ideas generated, modifications to the solution) and Google Docs for collaboration. A follow-up activity could include providing students with a sample Gantt chart that involves the development of a software solution. The Gantt chart includes tasks, start and end dates, duration, dependencies and milestones. Students compare this to the school calendar and determine interruptions and their own milestones in order to submit the solution on time. Conduct a class discussion on monitoring the project and the importance of coordination via the roles and responsibilities of group members.
- Watch the video 8 Apple design flaws that get under my skin and conduct a class discussion to critically analyse methods and techniques for testing a solution
Prepare a series of small case studies for students to research a range of legal issues involving copyright infringement, misuse of medical records and privacy breaches. Ask students to:
- identify the specific acts and the legal issues discussed
- explain what led to the legal issue occurring
- discuss how the legal issues could have been avoided
- present their findings in a table.
Example scenarios include: Apple vs Masimo over Apple’s smartwatch with blood oxygen feature; Apple vs. Samsung infringement case.
- Conduct a class discussion on the ethical issues involved with the use of current and emerging technologies. Examples could include significant contemporary issues, such as: unauthorised sharing of user information via social media; proliferation of surveillance technologies which includes facial recognition and location tracking; job losses (e.g. driverless trains).
- Assign students to work in small groups to research (and then present) an ethical issue arising from the use of artificial intelligence. Examples could include: deepfake technology; use of AI in healthcare (e.g. patient privacy, data security, potential for misdiagnosis); algorithmic bias (e.g. decision-making processes based on race, gender, socioeconomic group).
- Divide students into small teams to discuss and design appropriate evaluation criteria for evaluating the efficiency and effectiveness of a range of tablet devices.
Detailed example
Based on one of the learning activites (KK3)
Research activity on the impact of emerging technologies
This classroom activity explores the impact, including potential impact, of emerging technologies on society. Previously students would have studied the functions and capabilities of digital systems such as assistive technologies which can help individuals with disabilities or special needs perform tasks that would otherwise be difficult or impossible to do without assistance. However, emerging technologies can also have a negative impact on society, such as loss of jobs and a decline in physical human interaction.
One suggested approach to allocating class time to this activity is as follows:
- Teacher engages the class in a discussion, through use of a montage of images or short video clips of emerging technologies (e.g. Tesla’s autopilot, Amazon delivery drones, wearable plant sensors, net-zero-energy data centres) to explain that emerging technologies are new or developing innovations that have the potential to significantly influence/impact various aspects of human life, including work, communication and social interactions.
- Students are divided into small groups, and each group is assigned to a specific area of ‘impact’ to research, in the form of an overarching question, which provides the students with a framework for investigating the multifaceted impacts of emerging technologies. Examples include:
- How are automation technologies such as artificial intelligence and robotics changing the nature of work and employment?
- The car manufacturing industry has been significantly impacted by automation over the years. However, collaborative robots, also known as cobots, have the potential to revolutionise the car manufacturing industry. How are these cobots being used, and what will be their long-term impact?
- How does automation impact education and workforce training, including the need for new skills and competencies to adapt to changing job requirements?
- How do emerging technologies (e.g. artificial intelligence and machine learning algorithms) influence decision-making processes and productivity in various industries, such as healthcare, finance and/or manufacturing?
- Job displacement and deskilling/upskilling/reskilling are linked to advancements in technologies. What are the long-term impacts of emerging technologies on employment patterns, job roles, potential career trajectories, and the future of work?
- How have emerging technologies (e.g. artificial intelligence and machine learning algorithms) been used for malicious purposes, such as cybercrime, online harassment, fraud, the spreading of misinformation and propaganda, and identity theft?
- Remote work arrangements have been facilitated by emerging technologies such as teleconferencing and virtual collaboration tools, and remote access to data and resources. How has the use of emerging technologies affected the frequency and quality of face-to-face interactions among individuals and within communities?
- Emerging technologies can further exacerbate technology-induced isolation and loneliness. What are the impacts on mental health and wellbeing, and what improvements can be made to the way that these technologies are used?
- Information collected through group research is compiled and logically arranged in a multimedia presentation that will be delivered in the next lesson
- Groups present their findings. They share their ideas and conduct whole-class discussions
Unit 2 Area of Study 2: Cyber security
Outcome 2:
On completion of this unit the student should be able to respond to a teacher-provided case study to examine a cyber security incident or a network vulnerability, evaluate the threats to a network, and propose strategies to protect the security of data and information on the network.
Examples of learning activities
- Provide students with a case study scenario involving a security breach. Assign students to small groups and have them design a security strategy incorporating multi-factor authentication and Zero Trust Architecture, which they present to the class for discussion and feedback.
- Students design/draw/model/simulate/build a network using a router and other relevant devices such as laptops, tablets, smart phones, Raspberry Pi-based web servers or an Arduino wireless network to send and receive data.
- Students conduct research and prepare a report that compares and contrasts the strengths and limitations of wired, wireless and mobile communications technology.
- Conduct a guided tour of the school server room and network infrastructure under the supervision of the school’s IT or Network Manager. Prior to the tour, students develop questions to ask the IT staff regarding the internet, VPNs, school intranet, data storage and backups, hardware and software components and any network security-related issues.
- Discuss the applications and capabilities of LANs, WANs and WPANs. Demonstrate how to set up a WPAN using a mobile phone or an old wireless router.
- Discuss, using case study examples, the risks and benefits of using networks in a global environment. Case study examples can be drawn from media reports such as: Airlines suffer worldwide delays after global booking system fails; Overseas hackers take control of social influencer’s media accounts; and Facebook’s alleged privacy breaches.
- Watch the short video Malware: Difference between computer viruses, worms and trojans by KasperskyLab. Students research examples of malware attacks in the media. They write a report on the key technical features of the malware, the impact on the organisations that suffered them, and prevention strategies that should have been used or were developed as a result of the attacks.
- Assign students to groups and provide them with a hypothetical case study scenario, such as: ‘ABC Secondary School’s website was defaced with a message from an unknown group stating that sensitive staff information has been accessed and downloaded from the school’s server. Following an investigation, the school’s IT department determined that weak passwords and improper credential management were the likely cause of the attack.’ Each group analyses the main determinants and delivers a list of steps that need to be taken to address the issue.
- Analyse as a class the WannaCry ransomware attack, which exploited older versions of the Windows operating system, and affected organisations worldwide, including the UK's National Health Service.
- As a class, discuss the role of cryptography in an historical event, such as the World War II code-breaking efforts at Bletchley Park. In a follow-up activity, students work in small groups to solve a cryptogram puzzle, based on a Caesar cipher and/or Vigenère cipher.
- Introduce the concept of decision trees and their connection to machine learning algorithms, before assigning students to small groups to create a decision tree, based on a scenario, such as: ‘In deciding on a university course or vocational pathway there are several factors to consider, such as: course entry requirements, interests, strengths, job prospects, career goals, etc.’ Students brainstorm and list their criteria, which they use as the basis for creating a decision tree until a final decision (or choice) is achieved.
- Conduct a class debate on the legal and ethical aspects of ethical hacking and incorporate questions on responsible disclosure, bug bounties and the consequences of illegal hacking.
- Students work in small groups, each group assigned with one of the Essential Eight strategies. They create informative and visually appealing posters or infographics that explain the strategy, its importance, and how it can be effectively implemented. The posters and infographics are shared with other groups who are invited to ask questions and provide feedback. These can be placed on display in the classroom.
Detailed example
Based on one of the learning activities (KK10)
Bletchley Park and cryptography
The following sequence of activities can be used to introduce students to cryptographic techniques while also providing a historical link to the importance of Bletchley Park.
- Show the class the short video Code Breakers of Bletchley Park to provide a ‘hook’ for the lesson.
- Use the video as the basis for a class discussion on Bletchley Park and its historical significance during World War II and how it served as the center for British codebreakers who cracked encrypted German messages contributing to the Allied victory. Share anecdotes and stories about the codebreakers, including notable figures (i.e. Alan Turing).
- Introduce students to the concept of encryption and decryption by explaining that ciphers are used to encode and decode messages.
- Present the Caesar cipher and explain how it shifts letters of the alphabet by a fixed number of places (e.g. shifting by 5 so that A becomes F) to decode/encode text.
- Students complete exercises involving the Caesar cipher (decoding and encoding).
- Present the Vigenère cipher and explain how it uses a keyword to shift letters in a more complex pattern.
- Students complete exercises involving the Vigenère cipher (decoding and encoding).
- As a class, discuss the importance of pattern recognition and problem-solving as part of cryptographic techniques to protect data and networks.
Unit 3 Area of Study 1: Data analytics
Outcome 1
On completion of this unit the student should be able to interpret teacher-provided solution requirements and designs, extract data from large repositories, manipulate and cleanse data, conduct statistical analysis and develop data visualisations to display findings.
Examples of learning activities
- Students document how they can see artificial intelligence features being implemented into common software tools. Some examples of tools include the Microsoft 365 suite, Canva, Adobe suite and web browsers.
- Demonstrate the process, in a step-by-step example, of how to document solution requirements, constraints and scope for a small case study. Useful steps to follow are:
- asking questions of the users (what do you need?)
- observing and identifying what users are currently doing
- understanding mandatory changes that could be needed (legislation or crucial business need)
- knowing the systems and processes that will be impacted by any change, including manual.
- Using the following examples, demonstrate to students the reasons why specific data types are used to store data:
- Telephone numbers are best stored as strings because characters such as parenthesis or spaces are usually required for storage and no additional processing is needed. Mobile phone numbers regularly contain a leading zero that would be dropped when storing as an integer value.
- Sorting numeric values or numbers as text achieves a different outcome – 1, 3, 5, 15, 101 (numeric value sort) vs 1, 101, 15, 3, 5 (number sort as text) – due to text sorting not taking into account place value.
- Storage of a True/False value as 1 bit is more efficient than storing a string value representing ‘True’ or ‘False’.
Use a case study to transform a flat file of data from a large repository into a relational database. Provide a sample of data from the final database plus a list of steps that were required to transform the data into this state to help students understand the process, provide a sample of the data from the final data base plus a list of steps that were required to transform the data into this state.
Useful steps for students to follow are:
- interpret data requirements from the case study
- create database tables and apply validation including rules and input masks
- identify primary and foreign keys and link the tables
- import data for each table.
These could be completed with either a GUI-based RDBMS package, SQL or both.
Create a design for a simple database that includes relationships and keys; for example, one of the following scenarios or one of your own:
- a new and used cars sales business
- database of music files for a DJ.
Provide students with sample data records to insert into the database and an incomplete data dictionary that they are to fill in. They can refer to the sample records to fill in values such as field name, data type, size and validation requirements.
This allows students to revise skills of naming conventions, data types and electronic validation.
Provide students with a sample output from the database and ask them to write a query to produce this output.
- Provide students with a database with data imported and a list of data requirements for extraction. Students manipulate the data by creating SQL statements (queries) that meet the required data requirements. These requirements should include the following:
- selecting the correct data (SELECT statement)
- identifying the correct data source (FROM statement)
- using criteria to filter data (WHERE statement)
- using multiple criteria with Boolean operators (AND/NOT/OR)
- sorting (ORDER BY statement)
- linking tables (INNER JOIN statement).
Note: queries do not need to include each of these statements. Data requirements can gradually increase in complexity.
- Manually create a reference list in a document using the APA method for the following types of data sources:
- a website article with an author and date listed
- data from a website
- music
- a social media post
- a newspaper/magazine/book.
- Provide students with a spreadsheet with many rows and columns of data so that they can practise manipulating and cleansing data. Provide students with the following directions:
- Ensure each spreadsheet retains the original data in one tab – copy the tab to make any changes (may need to occur multiple times).
- Practise applying a filter (using text and numeric criteria) and using advanced sorting to a spreadsheet with over 300 records).
- Explore different ways of analysing data using spreadsheet functions to calculate summaries (average, sum totals) and measures of spread (standard deviation, median, range, maximum, minimum).
- Change the way that data is viewed.
Students are given a variety of charts where they need to identify what the r value is. Examples can be where r = 1, 0.8, 0.3, 0, -0.3, -0.8, -1
They can then link these r values to descriptions:
- perfect positive correlation
- strong positive correlation
- weak positive correlation
- no correlation
- weak negative correlation
- strong negative correlation
- perfect negative correlation.
Ideally, mix up the charts so that students can identify the correct correlation value and description for each chart.
- Explore the Information is Beautiful website and ask students to write the purpose of each visualisation (exploratory data analysis, information presentation or interactive), and the different types of data visualisations presented.
- Students research dashboards of information, guided by the information provided by Tableau. Students then locate online a dashboard for each of the industry areas.
- Students create a storyboard to document data changing over time for an animated (motion) chart. Examples of good uses of animated charts can be found in Flourish Studio.
- As a class, view a range of the infographic templates listed on the Venngage website. Discuss how each infographic format used improves the clarity of message. Students create a sample infographic mockup on a topic of their choice using one of the templates.
- Develop a testing table structure (test number, description of test, expected result, actual result) and ask students to design test cases that would help to ensure that:
- database validation is working for multiple fields when data is imported
- a spreadsheet has formulas that work correctly.
- Develop a testing table structure (test number, description of test, expected result, actual result) and ask students to design test cases that would help to ensure that:
- a data visualisation is effective in presenting the information (this can include formatting of data, text)
- a data visualisation is representative of the data (this ensures that correct data values are displayed).
Detailed example
Based on one of the learning activities (KK6)
Extracting data from an online repository using SQL
For this activity students will acquire data from a large repository. Explain to students the context of the World Bank World Development Indicators and how useful they are in understanding and analysing a range of economic measures. These assist experts to create policies to enhance world development.
Students can open a web browser and navigate to the World Bank’s databank.
The extraction of data from large repositories often requires the requestor providing structured instructions to receive the data they require. This links into how a Structured Query Language (SQL) statement can be created. This terminology is helpful to assist students understand the data extraction processes.
Students seeking to find data in large repositories will have to identify their database (part of an SQL statement’s FROM condition), specify fields required from a large list (part of an SQL statement’s SELECT condition) and only extract data that meets a specific set of criteria (part of an SQL statement’s WHERE condition). A template statement would be: SELECT fields FROM database WHERE conditions.
In the web reference, students use the data generator tool to specify the variables they require (on the left-hand side of the screen). They follow the steps below:
- Use the World Development Indicators database (FROM) and keep this option selected in the Databases drop down.
- Look for specific indicators or series to view (SELECT). This is where options need to be selected, for example GDP growth, unemployment rate, population, etc.
- Enter a specific list of countries (WHERE) with which to scope the study. Countries and aggregate areas are available in this chart. Individual countries are generally best selected for comparison purposes.
- Enter a specific list of points in time (WHERE). Appropriate scope needs to be considered for the amount of data to be analysed and displayed.
Students can be informed that the extraction tool uses Boolean and logic to find only data that exists for fields that satisfy both the requirements of country and dates. For example, if GDP data from Afghanistan from 2014–2021 is selected, only the data that meets these requirements is extracted.
Demonstrate to students that there are different formats of files for export that are generated by the database such as Excel, CSV and Tabbed Text. The data generated also includes referencing information that can be very useful when considering how reliable the data is. Each data source contains a reference from where it was collected.
Give students examples to interpret with the data generator. Provide indicators, countries and points in time. Allow students to increase in complexity the requirements of their queries.
For example:
- selecting the correct data (SELECT statement) – in this case Afghanistan but could include different or additional Country or Area of the world values
- identifying the correct data source (FROM statement) – in this case World Development Indicators but there are 85 data sources available for use in the World Bank Database
- using criteria to filter data (WHERE statement) – in this case 2014–2021 but could have additional years added where values exist
- using multiple criteria with Boolean operators (AND/NOT/OR) – in this case not used but could allow a comparison to be made between values in the 1980s by creating a condition that reads: 1980 > year > 1989 OR 2014 > year > 2021.
Students should extract data into each of the three format options.
Data can be sorted by one or multiple fields in a database, in either ascending or descending order. When this occurs in a database, an ORDER BY statement would be used.
Students should be made aware that they can use this method of expressing data collected from a repository. Students should be aware of methods of documenting data requirements because they will need to interpret these as part of Unit 3 Outcome 1 and they need to create requirements as part of their SAT (Unit 3 Outcome 2).
The data stored at the World Bank lends itself to data analytics of a range of very interesting data points over a period of time. Students can create charts (scatter, combo) that compare the impact of variables such as literacy rates, mortality rates and unemployment rates when overlaid with GDP data.
When sets of values are extracted from multiple database tables this can be completed using an INNER JOIN statement. A linking (primary/foreign) key relationship is determined between the database tables.
Consider an example where a database table (tblUnemployment) has the unemployment rate, the year and the country, and another database table (tblGDP) has GDP growth, the year and the country. To extract the unemployment rate, GDP growth, the year and the country (with some filtering and ordering of values), this would be a statement that can be used:
SELECT U.country, U.stats_year, U.unemployment_rate, G.gdp_growth
FROM tblUnemployment U
INNER JOIN tblGDP G on U.country = G.country AND U.stats_year = G.stats_year
WHERE U.stats_year > 2020
ORDER BY U.country DESC;
To practise using SQL, consider the use of an online SQL editor such as sqliteonline .
With two different values (in this case GDP and unemployment) that can be compared, it allows the opportunity to analyse correlations. This is best completed within a spreadsheet once the data has been extracted.
Unit 3 Area of Study 2: Data analytics: analysis and design
Outcome 2
On completion of this unit the student should be able to propose a research question, formulate a project plan, collect and prepare data, and generate design ideas and a preferred design for creating infographics and/or dynamic data visualisations.
Examples of learning activities
Teacher provides a general topic for the class. Related to this topic, students develop a research question that is clear and focused, can be researched and answered (feasibility) and provides an opportunity for analysis (measurable data requirements), rather than a description.
Check around the class for the originality of questions chosen. Can the answers to questions be found with a simple online search? Does complexity need to be added?
- As an aid to understanding project planning, students list all assessment tasks that are due in the next week / fortnight / month for each of their subjects (which can be used as milestones) and the activities that they need to complete at home to prepare for the tasks. Then they create a sequence for these tasks in order of urgency, and identify dependencies and allocate time for each task. Finally, they update this information to a Gantt chart so that they can identify the critical path and monitor the task they need to complete to succeed in their work.
Using the example of a car and a toaster, explain the functional and non-functional requirements of each. (A car’s main function is to carry passengers and luggage between locations safely. A non-functional requirement for a car is its colour, leather seats, how the power windows operate, sound system or top speed).
Explain to students that if a car cannot complete its main function, its other features are not going to make up for this deficiency. Relate this example to data presentation related requirements.
If a data visualisation does not contain accurate data and is not accurate to read, then its fonts, dynamic nature and colour schemes (examples of non-functional requirements) will not overcome the issue.
In a group discussion identify qualities of a data visualisation that would be functional requirements.
Develop an understanding of the data collection methods for primary sources. The first method is to use a survey requiring the use of an online tool such as Google Forms or Microsoft Forms. The second method involves writing questions for a face-to-face interview to be recorded on paper. The third method involves observing an event – examples could be the number of students walking in the corridors in the first ten minutes of the period or the number of cars of different colours in the school car park.
Conduct each of the surveys, interviews and observations with a small sample of students and compare the quality of the responses.
Students are given a list of data requirements from the Australian Bureau of Statistics (ABS) such as census data showing the population changes in Victoria (or a different topic of teacher choice). Encourage students to use the data requirements in the following activities:
- Search for data (through either the search tool, or finding the topic on the ABS home page) relating to the data requirements.
- Browse through a number of tables to find data in a suitable structure and format.
- Download into a file that can be imported into a database.
An added challenge would be for students to document each step of this process so that it can be repeated later on.
Students complete the following two activities to understand the progression from extracting data from a database into a spreadsheet form and then creating information:
- Compare the structure of a database (fields, records, highly structured) to a spreadsheet (rows, columns, loose structure) and list advantages and disadvantages of each structure type.
- Use a spreadsheet and create a unique tab that shows the format in which data needs to be structured to create different types of charts to be used in data visualisations (column, bar, pie, radar, world map, heat, etc).
By the end of this activity, students should have the confidence to process their own data from a database to a data visualisation using the flexibility of a spreadsheet to manipulate the data structure.
Teacher demonstrates how quantitative and qualitative data can be visualised. Discuss the difficulties in visualising qualitative data. An example is asking two questions to the class – ‘What is your favourite month of the year?’ and ‘Why is this your favourite month?’
The data for the first question, being effectively a closed question (predictable responses) can be easily transformed into a data visualisation (bar/column/pie chart) with categories of each month (Jan, Feb, Mar…). The data for the second question would most likely need to be grouped and summarised – coding of qualitative data before a similar data visualisation could be created.
Provide students with a range of data sets. Include data that is missing one characteristic of integrity (accuracy, authenticity, correctness, reasonableness, relevance or timeliness).
Check if the students can identify the characteristic for each data set.
For each example, discuss criteria that could be used to identify data that breaches these characteristics and methods that could be put in place to ensure the integrity of data.
As these criteria (on a generic level) could be used directly by students for their SAT, keep the focus on details specific to each data set.
Provide a data collection scenario: Students are collecting information from students in Year 7 using an online survey to be used by the Year 7 Coordinator to arrange better lunch-time enrichment programs.
Use these questions to guide students:
- What information would need to be provided to the Year 7 students? Or their parents?
- Is there a destruction date for the data? How is it to be stored and secured?
- How is the data going to be used? Who is the data going to be shared with?
- Does the data need to be de-identified? How can the coordinator be sure that every student has submitted their survey or that one student has not completed and submitted 20 surveys?
- Explain how the Copyright Act 1968 protects the rights of content creators. Students investigate – with specific interest in creating data visualisations and using images – whether there are any exceptions to the Act to allow free use for research purposes. Investigate the use of Creative Commons images and the restrictions that can still exist with these licences.
View how the APA referencing system acknowledges the use of artificial intelligence by students.
Discuss the implications of using artificial intelligence as part of student work. Show how organisations such as Monash University guide students in the ethical use and citation of artificial intelligence for research activities.
Discuss whether your school has rules related to the use of artificial intelligence for regular schoolwork. Do specific rules get applied for any assessment tasks, research tasks or all uses of artificial intelligence?
- Create a backup, archive and management system for your school files. Document each process that will be used as part of this system, whether automated or manual, cloud based or physical. Ensure the backup method(s) are identified.
Watch the videos How to Make Great Mood Boards found on Canva’s website (Creating Inspiring Mood Boards Online).
Students then generate a mood board for a specific topic of the teacher’s choice. See if there is diversity within the class by sharing after a set period of time.
Provide an opportunity for students to develop their own mood board for a topic of their own choice (but NOT related to their SAT this time).
As a class, discuss whether there is more diversity and creativity in the mood boards created with student topics or teacher-provided topics.
Provide students with a simple data set that enables them to demonstrate their ability to use data visualisation software.
Discuss with students how using data visualisation software can assist in fulfilling design principles listed in this key knowledge.
Allow students the time and opportunity to demonstrate each of these design principles and create annotations using text notes that demonstrate their ability to use data visualisation software.
Demonstrate how to construct a rubric for evaluating design ideas, using at least a high, medium and low scale for each area of assessment. Some examples of how a design idea can be evaluated include: ease of creation, ease of update, ability to be used on a range of devices (accessibility), ability to be used in both portrait and landscape formats and adherence to design principles.
Demonstrate how to create rubric entries for one of the evaluation methods and give students responsibility to create their own entries for other evaluation methods.
Direct students to now create another rubric for evaluating data visualisations (either infographic or dynamic data visualisation), referring to the Terms used in this study (pages 12–16 of the study design) for efficiency and effectiveness measures for software.
Provide students with a case study with sample design ideas and basic requirements listed. They create a design for a one-page infographic using a mock-up, and a sequence of three images for a dynamic data visualisation using a storyboard.
Examples of what the design ideas can provide include: the colour and the images to be used in the main infographic design, and time-based elements or a data set for the dynamic data visualisation.
Detailed example
Based on one of the learning activities (KK 1)
Develop a research question
Lesson 1:
- Teacher and students discuss examples of a research question and the qualities of a good research question:
- A good research question is clear and focused, is researchable (has measurable data requirements) providing an opportunity for analysis rather than description, has an appropriate scope – not too easy or difficult to answer, and is original.
- A good research question is clear and focused, is researchable (has measurable data requirements) providing an opportunity for analysis rather than description, has an appropriate scope – not too easy or difficult to answer, and is original.
- Teacher shows students a list of examples, including some that are high quality, some of low quality, and some that are high in some aspects and low in others.
- Students brainstorm three different topics that they are interested in researching. They find secondary quantitative and qualitative data that can assist in giving them additional knowledge when researching these topics.
- Students collect data or analysis articles and reports.
- Students summarise in one sentence the topic that has proved most interesting to them.
Lesson 2:
- Read through the Monash method for developing research questions.
- Students write a list of requirements for the data that would need to be collected for their topic in the SAT.
Lessons 3 and 4:
- Students should have found their topic and conducted some research. They narrow down their topic to a single issue or debate within the broader topic.
- Students write their research question. They need to find an answer to the question as they complete their project.
- Students work in groups to review each others’ research questions. Teacher provides students with some basic high-medium-low criteria to assist in this process. Examples of criteria that could be given to students are:
- Topic is interesting to student who has chosen it.
- Student has provided a range of secondary quantitative or qualitative information with which to research the answer to the question.
- The question can be answered (Yes/No plus reasons and evidence provided regarding why/why not?).
- The question has been scoped.
- The question can provide an analytical answer and is not just descriptive – using ‘how’ and ‘why’ statements instead of ‘what’ and ‘describe’.
- As part of this process, students provide feedback in High-Medium-Low format but refrain from giving direct advice to other students as to how to improve the questions. This is important when ensuring each student produces their own authentic work for this outcome.
- The Monash University web page contains three different and useful activities:
-
- understanding the value of scope on a research question
- learning how to narrow down a topic
- understanding how to phrase a question.
- After the research question has been generated, students work out their own data requirements incorporating project constraints and scope. The process outlined above provides some opportunities for some scoping to have already occurred and students can document this.
Unit 4 Area of Study 1: Data analytics: development and evaluation
Outcome 1
On completion of this unit the student should be able to develop and evaluate infographics and/or dynamic data visualisations that meet requirements and assess the effectiveness of the project plan.
Examples of learning activities
Documenting how data can be manipulated using software tools:
Review how changing templates and chart types using software tools (but maintaining the same data) can significantly alter the look of a data visualisation and make it more relevant to a target user.
Demonstrate how data can be manipulated for more efficient and effective use in creating a data visualisation. An example is using transpose arrows to swap rows and columns of data within data visualisation software. Hiding or deleting columns of manipulated data using a spreadsheet can also allow for only the data that is relevant being imported into the data visualisation software tool.
Discover methods where data is being transformed into data visualisations using artificial intelligence tools.
Creating findings based on a dataset provided by the teacher such as those provided for countries at Data Commons Place Explorer.
Teacher models downloading data for a topic – for example historical life expectancy in Australia - providing descriptive statistics through spreadsheet formulas to save students time. (If students need assistance calculating and using descriptive statistics for testing formulas, this can be supported with the use of this article from Simplilearn).
Students interpret the statistics to create findings about the data. These can start with descriptions (e.g. The average life expectancy currently is 83) and move to inferential (e.g. With current growth rates within the next 50 years, life expectancy can grow to over 100, which would need better aged care services in society.)
Teacher leads a discussion about the difference between physical and software security controls. Students list different physical and software security controls that can be used to protect files.
Students then should be able to describe the security controls for the files they keep for their schoolwork and identify areas for improvement. This can form the basis of an implementation plan or checklist, provided it includes information about who would add this security control, the benefits and description of the change to make, the priority of the change and the timeframe for updating.
- Review a range of business websites to see how organisations engage with specific audiences within the community. For each website, document characteristics, including age-appropriate language and images, cultural inclusiveness and gender inclusiveness.
- Provide students with a variety of examples of infographics and dynamic data visualisations. Include examples where the data visualisation occurs across more than one page. Students document:
- how the information is organised, including where on the pages text is included for clarity, what items are at the top/bottom of a page and the reason why items are in their position
- how multi-page data visualisations take the user on a journey through data and how data visualisation can be seen as data storytelling
- how long it would take for the data in the data visualisation to become outdated and less relevant and if data refreshes are required – detail the steps that would need to occur (where data is stored, queries and rendering of graphics that need to be re-run, manual vs automated, trigger on change or time).
Discuss different formats and conventions that will be used for a printed or static (black/white or coloured) data visualisation of different types (e.g. maps, bar charts). Formats are ‘the physical appearance in which data can be presented’, such as presentation style, arrangement shape and size. Conventions are ‘general or commonly accepted ways of working with digital systems or representing data to ensure consistency across a solution’, such as data alignment in cells and tables or using a consistent axis scale in a chart.
Tableau is a useful resource to help students understand how design thinking can make a data visualisation clearer for intended readers.
Students identify the difference between validation and verification by using both in an exercise.
Demonstrate, using a data entry form, how existence, type and range checking can be completed as the users add their data. Depending on the class capability, teachers can provide an example for students to annotate or ask students to create their own annotated diagram.
Provide students with some examples of sample data that would enter a system (receipts, statistical table) and then data visualisations that represent this data in a chart form. Students match the data visualisation with the source data and explain what has happened to transform the data (e.g. data grouped, sum functions used, queries filter the data, data visualisation occurs). Adding some errors to the data visualisations for students to locate can provide students an example of how a verification process can improve their end results.
An extension exercise for high achieving students is to understand some of the main features of data lineage. The article ‘What is data lineage?’ from IBM provides useful information.
A good test to see whether a data visualisation is successful is if the reader can grasp the main message within 30 seconds.
Provide students with a range of sample data visualisations and check whether they can write a one-sentence description of the main findings within two minutes. Ensure some data visualisations are unclear or misleading so that students can find the common features of good data visualisations.
Provide a reflection exercise for students to consider the importance of getting feedback from a range of potential users when creating data visualisations.
Teacher runs a discussion on the difference between an evaluation strategy and solution evaluation activities within the problem-solving methodology in the study design.
In groups, students prepare a 5-minute presentation to the class about:
- how clear criteria enables and requires the collection of data to be used when evaluating data visualisations
- the importance of knowing when evaluations are going to occur
- why ensuring that there is a responsible person ensures that evaluations are completed successfully.
- Using several different data visualisations, including at least one infographic and one dynamic data visualisation, model how evaluation criteria can be applied and evaluated. Ensure that students note down different data collection techniques that could have improved the evaluation. Show students how to determine if the data visualisation is efficient, effective, and is appropriate for a target audience.
Create a sample Gantt chart for the class that includes: a range of tasks, time allocations, dependencies and milestones.
Create a scenario/case study where tasks will not be completed on time, time allocations will be altered and milestones will occur later than planned.
Students annotate changes to the Gantt chart and document why the changes have been made and the impact of these changes on the project schedule.
Provide students with a sample document containing three columns: change made to project plan, reason why change is necessary, impact of the change.
Teachers enter sample data for these columns for a project. Four or five examples of where a change is needed to the same project would be sufficient for this exercise.
Model to students how to use this data to assess the effectiveness of the project plan in managing the project.
Detailed example
Based on one of the learning activities (KK7)
Validation and Verification
Using validation techniques within databases can help to ensure that data integrity is preserved and maintained when records are entered individually or imported in bulk into a database table. The example below is of a database table that has not been validated.
Sample data
| First Name | Birth Date | StoreRating | FavConsole | Member | |
|---|---|---|---|---|---|
| Joe | 2/02/2012 | joe@googlemail.com | 7 | Xbox | Yes |
| Carlos | 3/15/2000 | carlos.best@manu.com | Switch | ||
| Anton | 3/06/1918 | antonio.b@microsoftmail.com | 5 | Xbox | No |
| 14/03/2001 | filipe.sanchez@one.com | Four | Twitch | No | |
| Dejan | 24/04/1999 | dejan google | 11 | Playstation | Yes |
| Harvey | 5/23/1995 | hjs@yahoo.org | 4 | Playstation | 4 |
As part of this activity, the teacher provides students with a table of data similar to the one above. Validation techniques require careful design to ensure they are appropriate and do not reject valid data. Students are guided through the design process as part of the teaching and learning program to ensure that they can apply these techniques when completing the SAT.
The validation process should consider:
- the identification of database fields and their data types
- appropriate form controls that may assist with validation (list boxes, combo/radio boxes to limit input)
- appropriate validation rules.
Examples of appropriate validation rules include:
- every field should be required
- data types should be as per the types in the table
- Email should be entered correctly and represent a valid address (e.g. validation rule: Is Null Or ((Like "*?@?*.?*") And (Not Like "*[ ,;]*")))
- StoreRating needs to be between 1 and 10
- FaveConsole needs to be one of Xbox, Switch or Playstation.
Once students have designed their validation rules they identify records in the teacher-provided table that should not be accepted according to the designed validation rules, and explain why these records should not be added.
Verification is also important for completed data visualisations to ensure that data has integrity from collection to the time that the data is being visualised. If a chart were to be included in a data visusalisation that tallied the values for Store Rating and the chart looked like the one below, there may need to be an adjustment to the data values stored in the data visualisation software tool. Alternatively, in the original spreadsheet, depending on where the original error began. Can you identify the error/s?
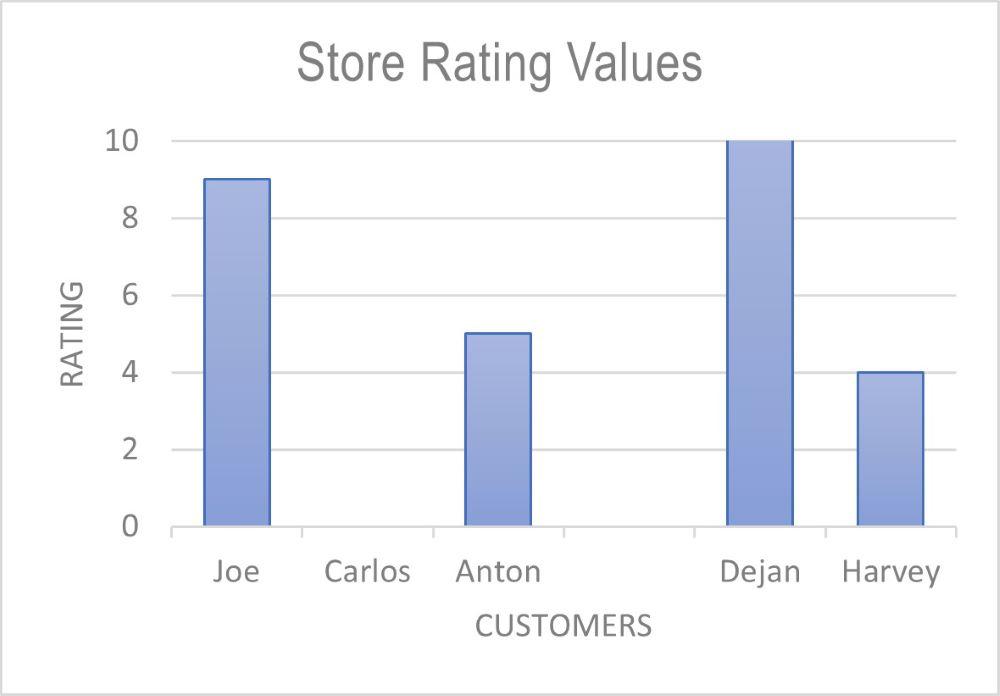
The activity could be extended to students importing data into the database table, noting which records were able to be successfully imported and where validation was successfully applied. Students also explain any failures in the validation process.
Teachers can also discuss the following questions as part of their teaching and learning program involving validation:
- Should unreasonable records be edited and re-imported successfully or ignored?
- How could a decision be made to correct a record? Use an example from this scenario to demonstrate your case.
- Who should make a decision to correct a record?
- How should notes be taken of records that have been changed as part of the validation process?
- Describe the best way to resolve an error picked up when verifying values.
Students can reflect on the activity and respond to the following:
- List the advantages of validating input data.
- Explain the difference between data validation and testing.
- Provide examples of the three types of validation checks (existence, type, range).
- Outline the potential difficulties and dilemmas encountered by data analysts when they ‘fix’ unreasonable data.
- Consider the data that may be collected as part of the SAT. Identify examples of data that may be considered unreasonable or poorly formatted and need to be changed.
- Consider the amount of time that has been provided for validation and verification testing as part of the project.
Unit 4 Area of Study 2: Cyber security: data security
Outcome 2
On completion of this unit the student should be able to respond to a teacher-provided case study to analyse the impact of a data breach on an organisation, identify and evaluate threats, evaluate current security strategies and make recommendations to improve security strategies.
Examples of learning activities
Students identify a list of recent high-profile data breaches that have occurred. They research the way that the breach was detected, and responses taken, and whether privacy was appropriately protected.
In addition, the resource ‘Engaging with Artificial Intelligence’ from the Australian Signals Directorate provides information about managing risks when using artificial intelligence within an organisation.
- Students are given a list of mission statements and a separate list of companies/organisations and asked to match them. They can then explore the websites of healthcare, education, business/retail and non-governmental organisations to identify their goals. They identify the main similarities and differences found in this research.
- In preparation for a class discussion, students take time to prepare a response and then discuss why data and information security needs to be taken seriously by organisations with reference to:
- data being an asset that requires protection
- business reputation (link to their values – most organisations include ethical statements on the topic of trust)
- legal requirements to their customers/users.
Provide examples of each of these three types of threats: accidental, deliberate and events-based. For each of these threat types, students:
- document the possible impact on both collected and refined information
- create a list of mitigation strategies that can be used to eliminate or greatly reduce the impact of these threats.
Examples of threats could include:
- staff member damages equipment, unintentional power outage, user access rights to files is insufficient to prevent inappropriate activity, unintended consequences of using generative artificial intelligence
- viruses/malware, hacks to break authentication – e.g. phishing, Trojan horse threat on program installation
- fire, flood, earthquake or extended power outage.
Discuss example where data does not have integrity by referring to the characteristics of data integrity. Discuss how these examples will cause an organisation to have significant concerns regarding their daily operations.
Examples for students to consider:
- inaccurate data
- data where authenticity is questionable
- incorrect data
- data with unreasonable entries
- irrelevant data
- data that is out of date.
Teacher provides examples of diminished data integrity in data stored by an organisation that has led to: loss of reputation, poor decision-making, financial loss, legal issues and impacted operations.
Students work in teams to brainstorm strategies for reducing these problems and then share their findings with the class.
Develop a rubric with criteria for providing an assessment of security strategies in various scenarios. Ensure the criteria includes, and can expand upon, these measures of effectiveness in the criteria:
- confidentiality of data – only available to users who should access it
- integrity of data – refer to characteristics
- availability of data to key users at the appropriate time.
- Create a table listing the Australian Privacy Principles (Privacy Act 1988), the corresponding Information Privacy Principles (Privacy and Data Protection Act 2014) and the Health Privacy Principles (Health Records Act 2001) that relate to the collection, communication and security of data and information. Underneath the table, students explain the main differences between each piece of legislation, including the jurisdiction and who the legislation applies to.
Provide students with the resource ‘The Notifiable Data Breaches (NDB) Scheme’ from the Office of the Australian Information Commissioner. In this resource (a PDF), for the question referring to Section 26WR, refer to Page 4 of the web page and the local relevant content.
Students write down the main points of each of the sections listed in this key knowledge area:
- Section 26WE – What is an eligible data breach?
- Section 26WF – When is notification unnecessary?
- Section 26WH – What does serious harm mean?
- Section 26WK – What information must be included in communications to those impacted by a data breach?
- Section 26WL – What are the three options for notifying impacted individuals?
- Section 26WR – What are the powers of the Australian Information Commissioner?
- Brainstorm a list of unethical behaviours that a member of an organisation could participate in when considering the following:
- data collection and use (data storage, data access)
- system availability
- pressure from supervisors
- selling a product
- when users have their data impacted by a cyber security incident (access / modification / deletion).
Students list the steps that an organisation would take to encrypt and decrypt on their storage devices. They explain whether this process should be completed manually or automatically and justify their response.
While doing this, they should look at how ciphers are used and which ciphers should not be used. They explain the times when keys are used to protect data, and when hashing functions are used.
A useful (if detailed) resource is produced by the Australian Signals Directorate.
- Discuss the reasons and potential consequences for organisations if they do not plan for:
- evacuating in the case of a disaster
- backing up data
- restoring data
- communicating with required individuals when a disaster or cyber security incident occurs
- testing that their disaster recovery processes are current, working and effective.
Security controls are defined in the Terms used in this study as ‘Hardware, software, physical equipment, procedures and electronic measures used to assist in the protection of individuals, systems, networks, organisations and data that is collected, communicated and stored.’
Brainstorm a list of security controls that can be used to protect data.
Conduct an in-class debate on the topic: ‘Physical security controls are more important than software security controls in keeping organisational data secure.’ Students could focus on biometrics vs encryption.
Detailed example
Based on one of the learning activities (KK7)
Assessing security strategies
Students develop a rubric containing criteria to provide an assessment of security strategies in a number of teacher-provided scenarios. These scenarios should include at least one effective and one ineffective security strategy in each of the three main effectiveness measures listed in the Terms used in this study on page 14 of the study design (confidentiality, integrity and availability).
Students construct a rubric by matching statements to the effectiveness measures, as in the example below.
Teachers provide students with a scenario or case study that highlights two effective and one ineffective security strategy.
Sample scenario
The Joylands Grammar School Council completes regular weekly backups, which are kept both on and off site, and tests the process regularly (every three months) to ensure that their data can be fully restored in the case of a significant event.
Each banking transaction is reconciled three months after the event to reassure parents that the organisation is worthy of trust when handling finances. The IT department at Joylands checks the access rights of members of the organisation to file folders to ensure that they are appropriate and current. A check is triggered by any formal change of role in the organisation.
Each month, there is a council meeting where future financial projects are discussed and the three-month-old reconciliation reports are provided as ‘the current state of the Joylands’ finances’. All data discussed at meetings is grouped into categories to ensure that the privacy of parents paying bills and benefactors providing donations is respected.
Students create, and then use their own rubric to assess the effectiveness of the security strategies of the organisation. As part of their assessment, students write a short comment that addresses reasons for their ratings and assessment.
Example detailed rubric:
| Effectiveness measure | Low level | Medium level | High level |
|---|---|---|---|
| Confidentiality | Data and information stored in file folders have insufficient software and physical controls to protect the organisation from loss or inappropriate access. Access rights can be outdated and incorrect. | Most files stored in file folders are protected using appropriate security controls. Occasionally access rights are found to be incorrect allowing members to access files, they should not have access to. | All files are protected using both physical and software security controls that are appropriately applied for the needs of the organisation. |
| On site backups are stored in the same server room. Off-site backups are kept with an organisation which has not been checked, but were the cheapest. | On-site backups are physically separated from key servers. Backups of data are stored off-site with an organisation who was checked thoroughly before a contract was entered. | On-site backups are physically distributed around the organisation and placed in a secure area. Off-site backups are stored with an organisation which is reviewed every six months. | |
| Integrity | There are a large number of inaccurate and duplicate records that cause inefficiency in the way the organisation runs. | Most data is stored well with limited inefficiency caused by duplicate and incorrect records. | Data is stored with a high level of confidence that there will be few duplicate records and that they have been received from reliable sources. |
| Unreliable sources are used to collect data and backups are taken in a random ad-hoc manner. | Data backups are scheduled but restoration tests are rarely conducted. | Data restoration for backups are regularly and successfully tested. | |
| Availability | All files are too old to be of relevance and may ensure inaccurate decisions are made by the organisation. | Some files are not current and present an issue for reconciliation or being useful for the organisation to make accurate decisions. | Every file contains current data for the organisation’s usage requirements and ensures accurate decision-making by the organisation. |
| Data cannot be retrieved from storage devices. Manual data entry is required to restore organisation-critical data and information. | Data can be retrieved mostly using documented procedures. Occasionally data is not able to be quickly restored due to location of backup media. | Data can be quickly and easily retrieved by the organisation using clearly documented procedures and readily available backup media. |
Unit 3 Software Development
Unit 3 Area of Study 1: Software development: programming
Outcome 1
On completion of this unit the student should be able to interpret teacher-provided solution requirements and designs and use appropriate features of an object-oriented programming language to develop working software modules.
Examples of learning activities
- Use safe and appropriate artificial intelligence (AI) tools to explore how they can be used to generate and optimise code, and debug and test modules. Demonstrate how AI tools can generate code quickly and how code can be refined based on subsequent prompts.
- Discuss the ethical issues associated with the use of AI tools and how developers can address these when developing modules or solutions
- Examine familiar software solutions (such as POS systems, ticketing systems, social media, video games or mobile applications) in order to identify solution requirements, constraints and scope.
Lead students in practising the development of writing problem statements and documenting problems that can be solved using a software solution.
For example, the PE department at the school is loaning out sports equipment to the students at lunchtime but not all students are returning the equipment. The Head of PE would like a software solution to be developed that can help keep track of the sports equipment being loaned out at lunchtimes.
Discuss a range of teacher-provided solution requirements and designs so that students can identify key features of the software design, the structure of each of the provided design tools and the relationship between the designs.
For example: teacher provides students with a small set of requirements and one or two designs. From the provided requirements and designs, students unpack where the requirements are present in the designs. They could also identify structural characteristics of designs, such as determining required inputs and outputs, indenting of pseudocode, the proposed properties of an object or column headings within a data dictionary. Students could also identify how the designs are linked to each other within the given scenario.
- Identify and describe specific uses for a range of data types. For example:
- Telephone numbers are best stored as strings because often characters such as parentheses or spaces are usually required to be stored and no numerical processing is required.
- Sorting numeric values or numbers as text achieves a different outcome – 1, 3, 5, 15, 101 (numeric values) vs 1, 101, 15, 3, 5 (numbers as text) – due to text sorting not taking into account place value.
- Australian currency should be stored as floating point values to two decimal places, rather than integers, because currency uses dollars and cents.
- Compare a variety of data structures, such as arrays and records, in relation to their structural characteristics (single data type, integer index or indices, compared to multiple data types and field index), and discuss how each may be applied in a range of scenarios. Demonstrate how these data structures may be implemented within the selected programming language.
- Compare the formatting and structural differences between plain-text (TXT), delimited (CSV) and XML files. Provide examples. Discuss situations where one particular format may be preferred over the others.
- Explore how common items or things can be transformed into objects by identifying relevant properties and methods/functions (abstraction). Explore whether the modelled objects can be simplified (generalisation) or whether sub-classes could be implemented (inheritance).
- Using a range of exercises and resources, provide opportunities for students to practise developing code samples and modules using features of the selected programming language.
- Compare how solution elements (variables, interface controls and code structures) may be named differently using Hungarian notation, camel casing and snake casing. Use the examples provided to highlight why using naming conventions is one component of good programming practice.
- Demonstrate the development of a simple software solution that incorporates the validation techniques of existence, range and type checking.
- Document practice programming exercises through the application of appropriate internal documentation, explaining the purpose of the modules, key features of the modules and the justification of the use of the selected processing features.
- Split students into two groups. Provide each group with a copy of the same code sample. One group’s code will include internal documentation, and the other will not. Ask the groups to determine what the code does as quickly as possible. Discuss how the inclusion of internal documentation improves the maintainability and understanding of the code provided
- Conduct a role-play with students to demonstrate the algorithmic behaviour of sorting, involving selection sort and quick sort and searching involving linear and binary searching.
Compare the differences between a selection sort and a quick sort in terms of complexity and efficiency.
For example: selection sort works by moving the smallest (or largest) value to its sorted position on each pass, compared to quick sort which uses a pivot and sorts the data into two sub-lists; this process repeats until values are in the correct position. The algorithm for quick sort is more complex and more efficient than selection sort.
- Discuss and justify the use of a searching technique (linear or binary) based on solution requirements, the search algorithm and the structure of the data (sorted/unsorted).
- Provide students with code samples with syntax and logic errors and have them identify the type of error present and suggest corrections that are required.
- Provide students with code that has the potential to throw runtime errors. Demonstrate how these types of errors can be mitigated against without reducing the efficiency or effectiveness of the code, such as using error handling, additional checks on variables being included in the code, type masking.
- Provide students with a series of algorithms and ask them to suggest where breakpoints or debugging statements could be used. These algorithms may, or may not, contain errors.
- Demonstrate how to construct appropriate and reasonable test data for different features of a programming language, and test cases for the purpose of identifying issues with modules. Use a table and include columns for the expected and actual output.
Note: Teachers should be aware that some of the teaching and learning activities provided as part of Applied Computing: Software Development Unit 3 Outcome 1 may also be suitable for Applied Computing: Software Development Unit 4 Outcome 1.
Detailed example
Based on one of the learning activities (KK 7)
Modelling common items or things
The key knowledge requires that students understand the key concepts of object-oriented programming (OOP), including abstraction, encapsulation, generalisation and inheritance. Providing opportunities for students to model how common things can be represented as objects is one way that the concepts could be understood before developing skills around implementing objects in code.
Abstraction
- Come up with a list of common items that students would be familiar with. Examples may include sea animals, birds, vehicles, toys, kitchen appliances, clothing, etc.
- Students select one of these items and then model how it could be represented as an object. They should identify the necessary data required to describe the item (properties) and any actions the item is required to perform (methods/functions). Provide students with 5 minutes to come up with the properties and 5 minutes to come up with the actions.
- As a class, discuss how each of the selected items have been modelled by the students. Invite feedback and discussion around how the modelled objects could be improved. Students should refine their objects based on the feedback received.
Generalisation and inheritance
- Based on the objects that students have modelled (or examples provided by the teacher), discuss how certain objects could be generalised or inherit properties/methods/functions from a parent class.
For example, an object that describes sea animals or birds could be generalised into an animals object.
- Provide students with time to explore how their models (or the examples provided) could be generalised or utilise inheritance.
As a class, invite discussion and feedback around student responses. Students should again refine their objects based on the feedback provided.
Unit 3 Area of Study 2: Software development: analysis and design
Outcome 2
On completion of this unit the student should be able to document a problem, need or opportunity, formulate a project plan, document an analysis, and generate design ideas and a preferred design for creating a software solution.
Examples of learning activities
- Using real-world examples, discuss why individuals and organisations have undertaken a range of software development projects. For example:
- public transport systems moving to modern ticketing systems
- organisations enhancing productivity and efficiency, and reducing costs, using artificial intelligence and automation
- free-roam virtual reality systems, video games and phone apps developed to address gaps in the market.
- Plan an activity where students prepare a brief considering a range of problems, needs or opportunities. Conduct a peer review session in the classroom where constructive feedback is provided by two classmates. Students then refine the brief based on the feedback received.
- With a particular project in mind, students develop a Gantt chart using software that includes a range of project management features. Discuss appropriate techniques for documenting the progress and modifying the project plan.
- Discuss a range of data collection techniques. Justify how and when each technique would be used. Provide examples of a range of data that could be collected.
Analyse a mini-case study or brief in order to identify functional and non-functional requirements and constraints. Discuss how these and other factors may impact the scope of the proposed solutions.
The Head of PE wants the borrowing solution to be an internet application that works in multiple browsers and able to be used on mobile phones/tablets.
Functional requirements
- to record who has borrowed equipment
- to record who has returned equipment
- to provide a report of students who have not returned equipment after two days (version 2)
Non-functional requirements
- reliability
- usability
- portability (version 2)
Constraints
- usability
- technical
How these impact scope
- solution may be released across several versions where compatibility with one browser is ensured first, before mobile phone/tablet access is developed.
- Identify the features of context diagrams, data flow diagrams and use case diagrams. Consider how entities differ from actors, data flows differ from interactions, and ‘includes’ differ from ‘extends’, in relation to their function within each of the relevant analytical tools.
- Prepare an activity where students examine parts of a data flow diagram and identify whether conventions have or have not been followed. In situations where conventions have not been followed, students must explain the issue with the part and provide an appropriate suggestion to correct the error.
- Analyse a case study and construct or complete a context diagram, data flow diagram or use case diagram, applying relevant conventions as necessary.
- Prepare a strategy to develop a software requirements specification, by analysing several software requirements specifications (SRS) examples. List and describe the key features required in the SRS (as listed in the study design).
- Explore how organisations meet (or do not meet) legislative requirements for intellectual property and ownership and privacy of data. This can be researched using anecdotes, media and online articles. For example:
- unpack privacy policies of social media organisations to understand who owns the data posted to social media
- analyse how organisations protect user data to meet legislative requirements (two-factor authentication, encryption)
- discuss how organisations that suffer data breaches have met legislative requirements.
- Discuss student file management strategies, highlighting both positive and negative approaches for the handling and management of files.
- Research different backup techniques and prepare a presentation highlighting the advantages and disadvantages of each technique. Provide students with a number of different scenarios. Students then recommend an appropriate backup strategy for each scenario.
- Provide examples of how government departments and private organisations secure and dispose of their data.
- Research and compile a range of design ideas that could support the redesign of an existing familiar solution, such as an operating system, productivity software, video games, browser or mobile phone application.
- Provide students with examples of criteria that evaluate different aspects of the efficiency and effectiveness of design ideas and solutions. These examples should also be provided in a number of forms (e.g. questions, statements, dot points).
- Provide software requirement specifications for students to examine. Students generate a range of design ideas for the proposed solutions using a range of software design tools, including data dictionaries, mock-ups, object descriptions, input-process-output (IPO) charts and pseudocode.
- Explore familiar existing solutions (such as POS systems, ticketing systems, social media, video games or mobile applications) and consider how affordance, interoperability, security and usability contribute to the user experience. Discuss how these characteristics affect software design and contribute to the efficiency and effectiveness of the solution.
- Provide students with an opportunity to identify how each of the design principles are present within the interface of an existing solution and then redesign the interface to address the principles (which may be deficient) and justify their modifications to their peers.
Detailed example
Based on one of the learning activities (KK 12)
Design ideas
The key knowledge lists ideation techniques and tools for generating design ideas. Teachers should provide students with opportunities to undertake ideation activities in preparation for the School-assessed Task (SAT).
Teachers can choose whether to provide students with a case study about a particular solution or allow students to choose a familiar solution that requires some form of redesign. Students should be guided through the following process to facilitate the redesign of an existing solution.
- Students choose the solution they want to redesign. This could be an operating system, productivity software, video game, browser, or mobile phone application. They should spend 5–10 minutes exploring the current solution (mostly focusing on the user interface).
- Students start by identifying the aspects of the solution that they want to improve or change. This could include user interface, functionality, or user experience.
Students then research similar solutions available. Students look at their design, features, and user reviews. They can also use resources like tech blogs, product review sites, and user forums. They should store annotated screenshots and notes to use later on in the process.
(Optional) Students could also ask for the opinions of their peers to confirm their thoughts around the need for changes.
- Based on their research, students ideate and generate design ideas using sketches, brainstorms, mood boards and mind-maps to represent the possible new designs. Students should reference their annotated screenshots and notes when ideating and generating these design ideas.
- Students evaluate their design ideas based on teacher-provided or student-created criteria focused on feasibility, impact on user experience and alignment with user needs.
- Based on the results of the evaluation of design ideas, students refine their design ideas before developing detailed designs.
Unit 4 Software development
Unit 4 Area of Study 1: Software development: development and evaluation
Outcome 1
On completion of this unit the student should be able to develop and evaluate a software solution that meets requirements and assess the effectiveness of the project plan.
Examples of learning activities
- Discuss how the interfaces of familiar existing solutions (such as POS systems, ticketing systems, social media, video games or mobile applications) have evolved over time in response to user needs (as part of user-centred design).
- Demonstrate how clear and concise code, and detailed internal documentation contributes to the efficiency and effectiveness of solutions.
- Construct scenarios that provide students with the opportunity to consider and justify the appropriateness of using particular data types, data structures and data sources in particular circumstances.
- Using a range of exercises and resources, students practise programming, incorporating a range of features of a programming language and appropriate data types and data structures.
- Research how code repositories, APIs and libraries are used by software developers and how AI-based assistants are changing software development practices.
- Examine software solutions that have already been created. Discuss where examples of validation techniques could be used.
- Provide students with a series of algorithms and ask them to suggest where breakpoints or debugging statements could be used. These algorithms may, or may not, contain errors.
- Demonstrate how to construct appropriate and reasonable test data for different features of a programming language and test cases for the purpose of identifying issues with modules. Use a table and include columns for the expected and actual output.
- Provide students with a framework or suggested areas of focus to use when planning, conducting and documenting beta testing. Students could also conduct research to form their own framework that includes the construction of a test plan and test scenarios, observation of the tests and documenting the results.
- Students select a school information system, such as the website or Learning Management System (LMS) and plan testing scenarios for a mock-beta test. In groups of four, they carry out the test. One or two students act as the test observers, with the others in the group carrying out the tests. The observers document test results and then discuss the outcomes as a group.
- Students recommend strategies for evaluating the efficiency and effectiveness of software solutions that have already been created, focusing on criteria to be evaluated, when the evaluation will take place and who will conduct the evaluation.
- Using a case-study focused on real-world solutions, model how evaluation criteria can be applied and evaluated. Provide students with opportunities to discuss how different data collection techniques could be applied to determine whether a solution is efficient, effective and has met the needs of users.
- Explore factors that impact project plans (scope creep, personnel changes and technical issues) and consider how these may impact their effectiveness.
- Create a Gantt chart for a class that includes a range of tasks, time allocations, dependencies and milestones. Generate a scenario where tasks will not be completed on time, time allocations will be altered and milestones will be later than planned. Students annotate these changes on the Gantt chart and document why the changes have been made and their impact on the overall project.
- Using the annotated Gantt chart from the previous activity, provide students with a framework for assessing the effectiveness of their project plan. This could be undertaken individually or in pairs. Discussing how each change impacted the completion of the project and how changes could be avoided in future projects.
Note: Teachers should be aware that some of the teaching and learning activities provided as part of Applied Computing: Software Development Unit 4 Outcome 1 may also be suitable for Applied Computing: Software Development Unit 3 Outcome 1.
Detailed example
Based on one of the learning activities (KK 5)
Data validation
The key knowledge lists validation techniques that students are required to identify and use within solutions. One context where validation is frequently encountered is through the use of online services.
Online services frequently request data from new users during the user registration process. Most students and teachers will have experienced and used these registration processes that incorporate a range of validation techniques.
Discussion of good and bad validation experiences
Teachers identify and provide examples of different validation techniques used across a range of software and websites. Students highlight their own experiences with both good and bad validation. For example:
- Good validation techniques may include a list of states or countries, or the acceptable postcode format being updated after the user selects their country of residence.
- Poor validation techniques may include non-specific error messages being provided to the user when invalid data is entered or unreasonable logic being applied to the field being validated.
In relation to identified poor validation techniques, students provide suggestions as to how the validation could be improved to enhance user interactions with the solution.
Analysing scenarios to suggest how validation can be incorporated
Teachers also provide scenarios where validation has not yet been applied. Examples include:
- web forms
- modules that calculate the result of a formula based on user input
- log-in screens with specific requirements that have not been applied.
These scenarios are practical examples of real-world problems. Students work individually or in groups to justify and discuss validation techniques that could be appropriately applied to these scenarios.
Unit 4 Area of Study 2: Cyber security: secure software development practices
Outcome 2
On completion of this unit the student should be able to respond to a teacher-provided case study to analyse an organisation’s software development practices, identify and evaluate current security controls and threats to software development practices, and make recommendations to improve practices.
Examples of learning activities
- Students explore the websites of familiar medium and large healthcare, education, business and retail organisations in order to identify their goals. They propose a number of objectives that meet these identified goals.
- Discuss and debate the advantages and disadvantages of in-house software development vs external development, based off research from the internet and media articles.
- Present examples of how each of the vulnerabilities and risks listed in the study design introduce risks to development environments and software solutions. Examples are available through sources such as Australian Cyber Security Centre, Ars Technica, IT News, IT Wire and The Hacker News.
- Discuss how the use of physical and software security controls can protect software development practices. For example:
- Version control techniques, such as file naming, network storage and cloud services, can be used to ensure that the most recent solution files are being used and maintained.
- User authentication and credentials, such as device/network log in/passwords, biometrics, and multi-factor authentication, can be used to restrict access to systems/networks and protect spaces within systems/networks.
- Encryption can be used to protect data that is being transmitted across or stored on systems, networks or the internet.
- Ongoing code reviews can be used to mitigate the risk of vulnerabilities being overlooked when updates to code are made.
- Software patches and updates can be used to rectify identified application vulnerabilities, which in turn, improve the security of systems and networks.
- Separate environments are typically used to ensure that the risk of faulty or malicious code being introduced to production environments is minimised.
- Prepare a presentation that outlines threat-modelling principles and how these may be applied within medium and large organisations when looking to minimise risk to software development projects.
- Provide students with examples of criteria that evaluate the security of software development practices. These examples should be provided in a number of forms (e.g. questions, statements, dot points). For example:
- The development of the solution will be protected using a range of security controls.
- To what degree will the existing security controls protect software development practices?
- The development of the solution will be protected using a range of security controls.
- Conduct a ‘jigsaw’ activity where students research each of the legislation and frameworks listed in the study design, and then discuss and share their findings with their peers.
- Propose a number of ethically challenging scenarios to students, facilitating discussion and debate, asking them to clearly justify their position. For example:
- a developer realising that they have accidentally exposed customer data in a publicly accessible development environment
- using AI tools during the development of a solution and not performing due diligence on the code to ensure that it is free from vulnerabilities
- a developer uses code acquired from a code repository in a solution they are working on and does not acknowledge the owner of the repository’s work.
- Use game-based learning (such as PBS Nova Labs’ Cybersecurity Lab and US Department of Defense’s Cyber Awareness Challenge) to develop an understanding of threat/vulnerability mitigation measures.
- Based on a mini-case study, students develop a risk management plan that focuses on a hypothethical software development project and consider how practices could be improved to reduce the risks present.
Detailed example
Based on one of the activities (KK7)
Jigsaw activity
The key knowledge lists a range of legal and industry frameworks that affect how organisations develop software and control the security and communication of data. Students are required to familiarise themselves with these frameworks in order to be able to discuss them when applying their knowledge in School-assessed Coursework (SAC) and the end-of-year examination.
A jigsaw activity can be useful for engaging students with legislation and frameworks, developing collaboration skills and enhancing critical thinking through knowledge synthesis. Students should be guided through the following process to facilitate this activity.
- Provide students with some background around how legislation and frameworks impact the software development process.
- Divide the class into 5 groups (one group for each legislation/framework).
- Each group researches their assigned legislation/framework (approximately 30 minutes). They should focus on understanding the key points and their impact on software development practices.
- Groups prepare a presentation to communicate their findings to the class (approximately 15 minutes). The short preparation time is to ensure that groups are communicating their findings in the most efficient manner. Groups should prepare for questions and discussions after each presentation.
- After all groups have presented, facilitate a class-wide discussion. Ask students to reflect on what they’ve learned, how the legislation and frameworks might impact their work as software developers and any common themes or interesting contrasts they have noticed across the different legislation/frameworks.
Conclude the activity by summarising the key takeaways from each presentation and the class discussion. Teachers may also assign a reflection task for home study where students write a short paragraph about what they learned from the activity.